
Tim MalcomVetter
Co-Founder / CEO
Left and Right of Boom
NOTE: This is a reboot of my original article on this topic 5 years ago.
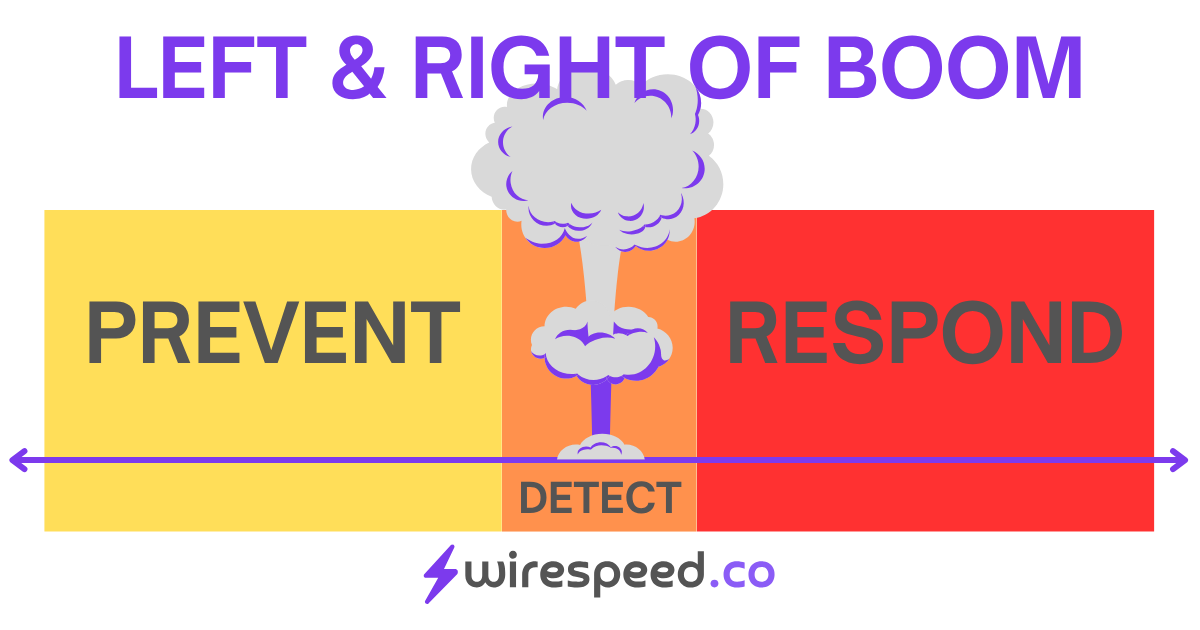
#What is Left and Right of Boom?
Left and Right of Boom is a simple concept that at first blush may just seem common sense, but it is a powerful mental tool to approach cybersecurity from both the offensive and defensive perspective. Some sources swap the word “boom” for “bang” but the meaning is the same. This concept is borrowed from the military (even if that isn’t your thing, there’s still value for you applying this to cybersecurity) and can be found in its original application in popular culture books like these:
-
Left of Bang: How the Marine Corps Combat Hunter Program Can Save Your Life
-
Left of Boom: How a Young CIA Case Officer Penetrated the Taliban and Al Qaeda
At its core, “boom” or “bang” is an unwanted event: the initial contact from the adversary. Left of Boom is the set of events that occur in the timeline before the the adversarial event and Right of Boom is the set of events that follows. Very simple. Left is the defender’s opportunity to prepare for and hopefully prevent boom. Right is when prevention controls don’t matter anymore; the reality hits you and you have to do something. Do nothing and the adversary wins.
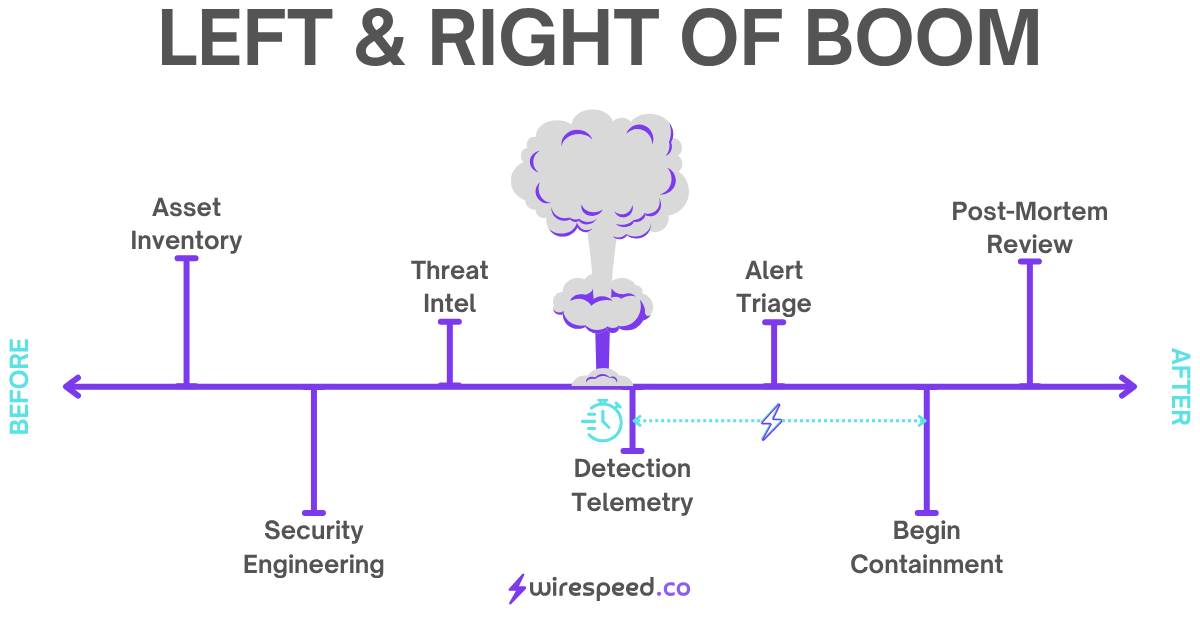
#The Model at a High Level
-
Left of Boom starts with Asset Inventory. It’s not exciting, but it’s paramount. You cannot secure what you do not know you have.
-
Security Engineering is the catch-all bucket for deployment, refinement, and hardening of all security controls.
-
Threat Intel is the idea that knowledge of the adversary’s practices may aid you in Detection.
-
Boom! An unwanted, adversarial cybersecurity event has occurred.
-
Right of Boom begins with Detection Telemetry as there is always a slight delay (see below).
-
Alert Triage is the process of assigning a verdict to the alert for “boom,” i.e. is it actionable or dismissable?
-
From there, a defender begins Containment of the adversary’s initial access attempt and any additional access gained through exploration.
-
If successful, the defender can then perform a Post-Mortem Review of the overall timeline to go back to Left of Boom to improve defenses in an informed cyclical loop.
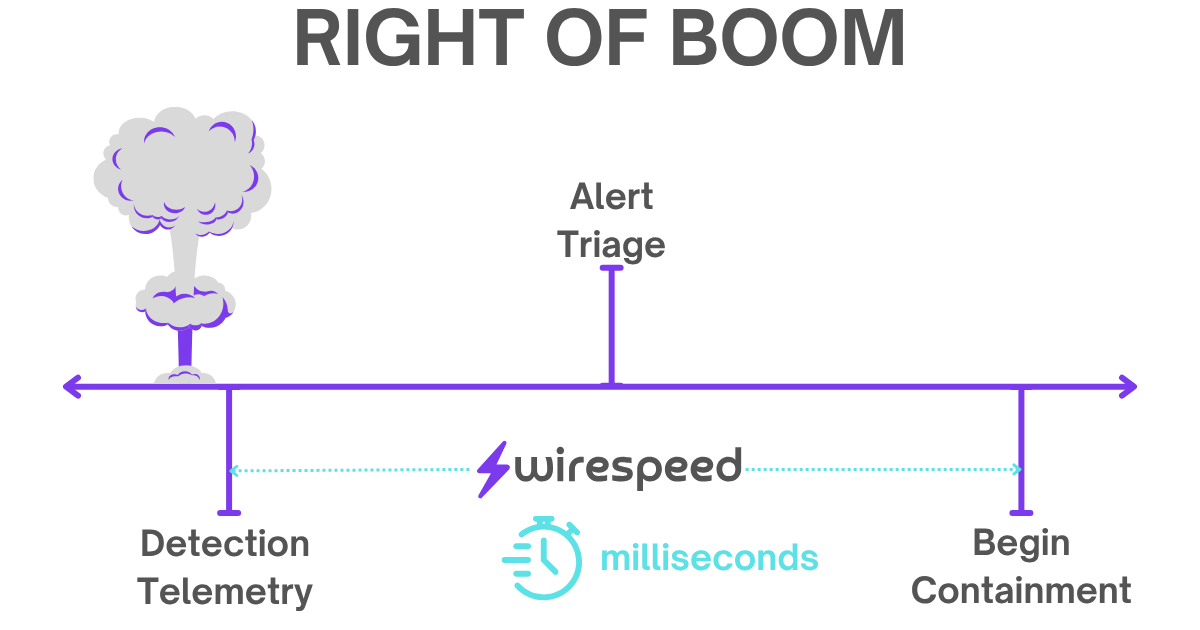
#Right of Boom
In general, the shorter the time/distance on the Right of Boom side from Detection to Containment, the less opportunity for the attacker to cause maximum impact and achieve objectives.
In some really large-impact and high-visibility breaches, the timeline between Boom and Containment is moot, because detection happened long after the adversary reached their objective (e.g. ransomware as discussed in “Adversaries are Speeding Up”).
Contrast this to security incidents the public never learns about: when the defenders are equipped and ready to detect and contain their adversary with a very short Right of Boom. No objective achieved. Did an infiltration happen? Yes, sort of, but it was meaningless without the adversary achieving their malicious objective. The only impact to the victim is the necessary expense of Detection and Response.
Wirespeed exists to make this the reality for our customers!
#Speed
I’ve been obsessed with the concept of “speed” in its application to cybersecurity since before the time I wrote the original Left & Right of Boom post. You can see that illustrated when I guided my Red Team to think algorithmically so they could stay ahead of defenders’ ability to respond, and then later when I dealt with the same topic from the defender side, defending hundreds of enterprises at once in a large SOC. You can also see my obsession with speed in the article I wrote advising red teamers to become software developers (“The Future of Adversaries is Software Development”), because you cannot be fast doing things manually. Software must do it for you.
Speed (being faster than the adversary) is at least half the the battle to master the Right of Boom. The other half is accuracy (more on that below).
Mastering Right of Boom requires two things: 1) being faster than the adversary, and 2) being accurate.
#Mean Time to Detect
There is always some sort of delay involved in all detections (which is why in the graphic above, detection is slightly Right of Boom). Bandwidth and compute are required to process one (or several correlated) raw events into a single detection.
It’s actually worth a tangent here:
Every security control is really a detection control at it’s core.
For years now, I have contended there isn’t actually such thing as a prevention control. Every security control is really a detection control, some controls just have predetermined and automated response mechanisms which appear to prevent bad things from happening. Every “bad cyber thing” has a Detection delay. Some are measured in milliseconds, others maybe hours, days, or even weeks (e.g. when a ransom note is first seen). When the Detection is Fast and the Response is Predetermined, we think of it as a “Prevention Control.” For example:
-
A web application that prevents XSS or other injection attacks is really just good at detecting invalid inputs and responds by discarding the content before it can be injected.
-
A firewall rule designed to block a port is simply detecting unwanted traffic by its protocol and port number and responding by dropping or resetting the connection request.
-
An AI security product classifying a response to an LLM chatbot as having sensitive data in it, then blocking the response with a “I’m sorry, but I can’t answer that” response.
This distinction is not just a nitpick — it ties in well with the Right of Boom concept. The “prevention” control detects boom immediately and responds without delay by mitigating the impact from the boom. There are really two events in the timeline, but they are so close together they are practically indistinguishable until you put them under the proverbial microscope (i.e. down at the code level).
#Mean Time to Verdict (Triage)
Not all detections are an actual “boom”. The Triage process aims to produce solid verdicts: either the alert warrants action or it doesn’t (i.e. it’s a false positive or an expected or acceptable event). This is the Accurate part of Mastering Right of Boom.
Historically, Mean Time to Verdict has been a human scale measurement, meaning humans had to review each alert or at least review the alerts that survived an initial automated screening process to eliminate some of the false positive noise.
Wirespeed produces Verdicts without a human inside the runtime decision process. Humans supervise and assure quality, not triage individual alerts, whack-a-mole.
#Mean Time to Contain
After a detection receives a verdict of actionable, the urgency transitions to properly containing the threat. If the defender is unsure how to contain a given threat, the Time to Contain will be slow and allow the adversary opportunities to out-maneuver the defender. If the containment process is defined, automated (at least mostly automated), and decisive, the defender will prevail, and the adversary will move on to other victims.
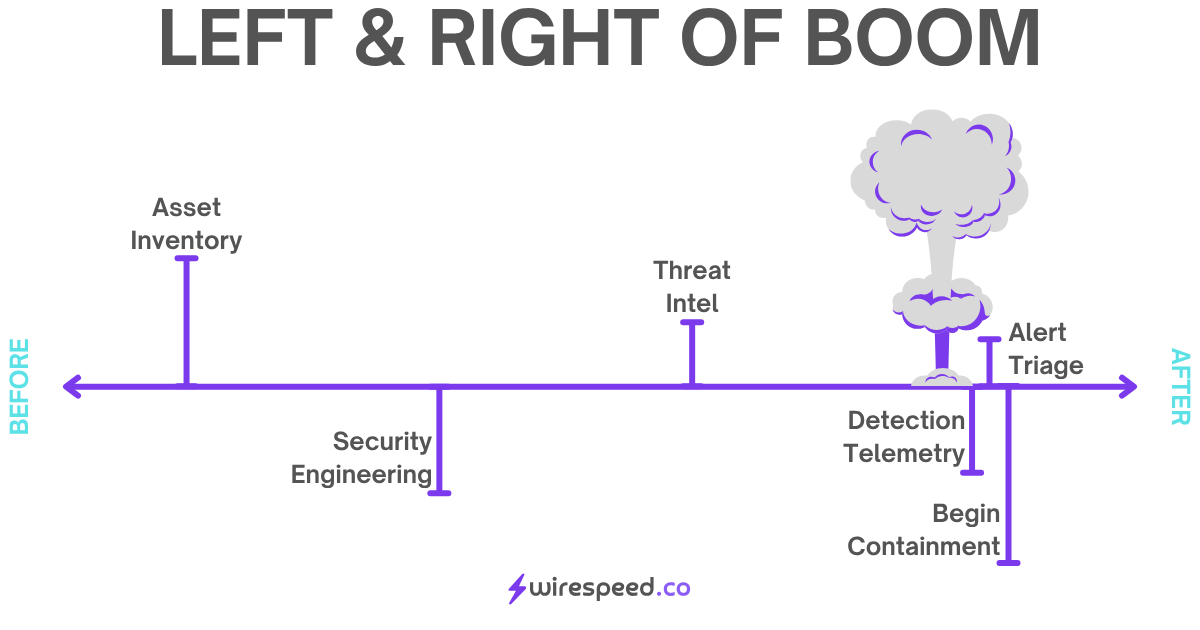
#Compressing Right of Boom
Putting this in action will result in a timeline that looks like this (tightly compressed on the Right of Boom side). Wirespeed aims to compress this down to seconds or less:
#Adversarial Decision Making
Adversaries also think in terms of Right of Boom. After an adversary gains initial access to a victim’s environment, they have their own timeline to address: the amount of time it takes to reach their objectives (e.g. ransomware), or at least escalate persistent access to give them even more time. Obviously, if the defender’s Time to Containment is fast enough, then the adversary will be unable to cause harm. Typically, for the adversary, speed and stealth are mutually exclusive, but moving fast against an under-prepared defender can be worth the loss of stealth!
Smart adversaries assess their tradecraft using the Right of Boom timeline to decide on a course of action. Suppose an adversary has Tactic A and Tactic B to choose between. If the adversary can predict that Tactic A will be detected and then contained immediately Right of Boom (before anything useful can be gained by the adversary) and Tactic B will be contained significantly later in the Right of Boom timeline (if at all), then the adversary will choose Tactic B. The most successful (infamous?) adversaries are excellent at collecting this data through repeat compromises to inform their tradecraft decisions.
So the best defenders must be faster than most effective adversaries … Wirespeed fast.
#Be Wirespeed Fast
We built Wirespeed with the critical understanding of Left/Right of Boom in mind. That’s why we aim to triage all detections to accurate verdicts as fast as the wires behind our compute will let us! In our current tests this is often in milliseconds and containment can be as fast as an API call after that.
When minutes or even seconds count, you have to know what you’re going to do with the alert before it arrives (i.e. have a planned process that includes all scenarios), and execute that plan vigorously. We have that plan and would love to cut your MTTRs down.
Circling back to the tangent/idea above, that a Prevention control is really just a Detection control with a fast, decisive, and accurate response ready to go, Wirespeed aims to flip the paradigm of Managed Detection & Response (MDR) on its head: we will detect, verdict, and contain so fast that someone new to cybersecurity may actually consider us as a Prevention control.
Want to know more about Wirespeed? Follow us on LinkedIn / X or join our mailing list.